What is CVE and CVSS
- BenQ
- 2020-04-26
Before we start our discussion, we must explain the term “vulnerability”. In terms of electronics, there is really no set standard by which to define the term “vulnerability”, as definitions vary among different organizations and research groups. Take the examples below:
1. The National Institute of Standards and Technology (NIST) in their NISTIR 8138 draft document defines a vulnerability as “any weakness in the computational logic found in products or devices that could be exploited by a threat source.”
2. The Open Web Application Security Project (OWASP) defines a vulnerability as “A vulnerability is a hole or a weakness in the application, which can be a design flaw or an implementation bug, that allows an attacker to cause harm to the stakeholders of an application. Stakeholders include the application owner, application users, and other entities that rely on the application.
3. The Common Vulnerabilities and Exposures List (CVE®) defines a vulnerability in general as “a weakness in the computational logic (e.g., code) found in software and hardware components that, when exploited, results in a negative impact to confidentiality, integrity, OR availability.”
We will focus our discussion on introducing the CVE organization and their definition of “vulnerability”
CVE is a cybersecurity database that collects and stores all types of cybersecurity vulnerabilities and exposures, giving each a serial number and making them publicly available for research and analysis. CVE is maintained by the MITRE corporation’s U.S National Cybersecurity Federally Funded Research and Development Center (FFRDC) and at present is the leading global database of vulnerabilities approved by the cybersecurity industry and corporate world.
Anytime a product, hardware or software, needs to be tested for security vulnerabilities, it is checked using the CVE website. When white-hat hackers or researchers discover vulnerabilities, they submit it to CVE who then announce it to the world with the goal of making users aware of the situation and push manufacturers to put their corporate responsibility into practice by developing a fix for the vulnerability.
An example of this process is when Google disclosed a vulnerability in Microsoft Internet Explorer and Edge web browsing software. In the incident Google’s team of security analysts, codename Project Zero, exposed a vulnerability in both 32-bit and 64-bit versions of IE as well as Edge that could lead to crashes in the browser along with remote attacks and/or take-over of the system’s hardware. Initially Project Zero revealed the vulnerability directly to Microsoft, giving the company 90 days to develop a patch to address the issue, but after Microsoft was unable to come up with a fix in the given amount of time Google revealed the bug to the public. The vulnerability itself was a so-called “type confusion flaw” that occurs in the HandleColumnBreakOnColumnSpanningElement parameter, and was eventually given the CVE serial number, CVE-2017-0037.
Each vulnerability published on the CVE database is assigned an individual serial number with the format, CVE-YYYY-NNNN, where CVE is a fixed prefix, YYYY is the year it was published, and NNNN is a sequential number (in principle this number only has four digits, but it can be increased to five or more digits when needed). For example, the Heartbleed Bug discovered in 2014 was assigned the serial number CVE-2014-0160.
Anyone can go to the website https://cve.mitre.org and click the search link or download a list of all vulnerabilities published in their database.
BenQ utilizes the CVSS standard of scoring vulnerabilities to assess their severity. For more details refer to the explanation below:
CVSS
• The Common Vulnerability Scoring System (CVSS) is a framework for rating the severity of security vulnerabilities in software.
• Proposed by NIST(The National Institute of Standards and Technology) was founded in 1901 and is now part of the U.S. Department of Commerce).
• Now operated by the Forum of Incident Response and Security Teams FIRST(Forum of Incident Response and Security Teams)
The current version of CVSS (CVSSv3.1) was released in June 2019.
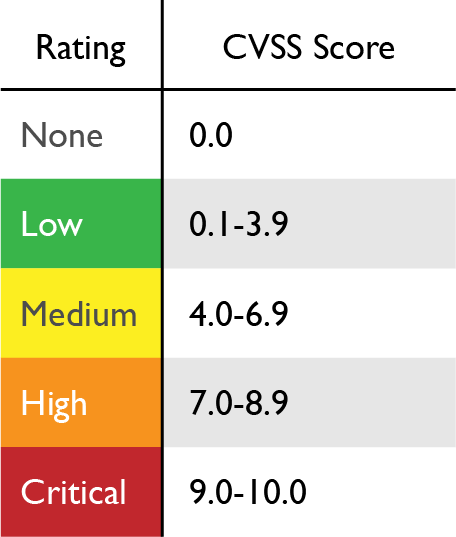
Scores are calculated based on a formula that depends on several metrics that approximate ease of exploit and the impact of exploit. Scores range from 0 to 10, with 10 being the most severe. While many utilize only the CVSS Base score for determining severity, temporal and environmental scores also exist, to factor in availability of mitigations and how widespread vulnerable systems are within an organization, respectively.
In order to ensure the security of your data transmissions, we recommend that before consumers purchase a product they use CVE to search whether said product has any security vulnerabilities and thus put to rest any doubts they might have about their purchase.